Oauth2 Authentication Workflow
Oauth2 authentication involves a 2-tiered authorization process. User access to open Interactions is controlled by an application key, which is defined in the Jacada Interaction Server Admin Console and embedded in the user's mobile application. Secured Interactions, on the other hand, may be accessed only by users who are authenticated against a 3rd party server. This second level authentication process includes both logging in and providing an access token.
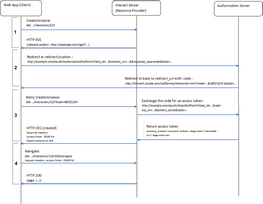
The full second level authentication flow involves 4 phases, which are presented in the following diagram.
Phase |
Process |
|---|---|
1 |
The user requests access to a secured Interaction, and is redirected to the Login page. |
2 |
The user logs in against the authorization server, and the client is provided with an authentication code. |
3 |
The client presents the code to the Interaction server. The Interaction server sends the code to the authorization server, where it is exchanged for an access token. The access token is returned to the client. |
4 |
A second request for the secured Interaction (using the access token) is sent to the Interaction server, and the Interaction is returned to the client. |